Zone - Endpoint Data Protection
One Zone Endpoint Data Protection protects the organization's endpoint from data leakage through Identity and group-based policy controls, encryption, shadow copies, logging, reporting and archiving. One Zone offers data protection and asset management in four easy-to-deploy and use modules:




- Data protection and Encryption
- Device Management
- Application Control
- Asset Management
These modules enable organizations to limit access only to trusted devices, applications and recipients while sharing data. Asset Management eliminated the IT burden on organizations with reduced support calls due to malware attackes, system recovery and performance isues. The easy-to-manage One Zone Endpoint Data Protection allows organizations to prevent data loss, enhance security, employee productivity and efficiend management of IT assets while retaining business flexibility. In addition, organizations can meet regulatory and security compliance requirements.
Benefits:
- Prevent endpoint data leakage.
- Extend data security beyond the network.
- Enhance employee productivity by blocking unauthorized applications.
- Streamline IT infrastructure management.
- Lower Total Cost of Ownership of IT infrastructure.
- Reduce malware penetration through patch management.
- Meet security compliance with IT asset management.
- Reduce legal liablity and business losses.
.png)
Application Control
Features:
- Offer granular, policy-based application controls for chat, webmail, gaming, file sharing, FTP and more.
- Apply policies even when offline.
- Set alerts and their levels for unauthorized application access.
- Customize warning messages to users.
- Set expiry time to disable temporary policies

.png)
Device Management
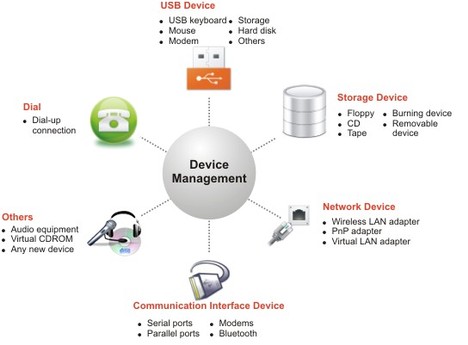
Features:
- Allow/block access to classified removable devices.
- Apply device control policy even when offline set expiry time to disable policies automatically.
.png)
Asset Management
Distributed offices and rise in malware attacks are opening organizations to higher levels of threats, leaving IT teams in a fire-fighting mode. One Zone's Asset Management module for Windows enables organizations to streamline their IT infrastructure management with centralized and automated hardware and software asset management that includes inventory, patch and update management. This allows organizations to control hardware and software costs while lowering malware penetration and meeting the requirements of security compliance.
Features:
- Hardware and software inventory.
- Hardware/software asset location, configuration, version tracking, historical information.
- Automated patch management, updates of Microsoft Operating System and its applications.
- Centralized management.
- Remote deployment of Microsoft Software Installation (MSI) packages.
.png)
Data Protection and Encryption
Insider access to sensitive documents and accidental or malicious fle transfer is a major cause of data loss. With the One Zone Data Protection and Encryption. organizations can control data transferred to removable devices, printers, or attachments in emails or over Instant Messengers. They can control document operations, document sharing and save shadow copies at the time of specified actions to the document. Organizations can eliminate the risk of data loss on account of lost removable devices by encrypting removable devices and files at the time of copying them to a device. They can ensure that data in devices is accessible only to authorized users through decryption requirement for encrypted files.
Features:
- Blocks file transfer by filename or extension over removable devices, Chat, Email, File sharing applications and more, Network sharing, Printers and etc.
- Specify read-write access to white-listed removable devices.
- Offer encryption and decryption for files and removable devices.
- Control file transfer via email and Instant Messengers based on file name, extension, size, within and outside the network.
- Control access to printers.
- Create shadow copies of files during creation, modification, transfer, print.
- Offer customizable alerts to administrators and warning to users.
- Create logs-reports of access, usage, modification, transfer and deletion of files.
Safeguard your endpoints and critical data with our Endpoint Data Protection services. Please contact us to learn more about our solutions or to discuss your data protection needs.








